What Is Encryption Technology
7 advantages of using encryption technology for data protection 5 simple data protection tips Encryption towards breaches coalition
5 Benefits of Using Encryption Technology for Data Protection
What is data encryption? Encryption technology data advantages protection Encryption requirement
Encryption & decryption... what are these?
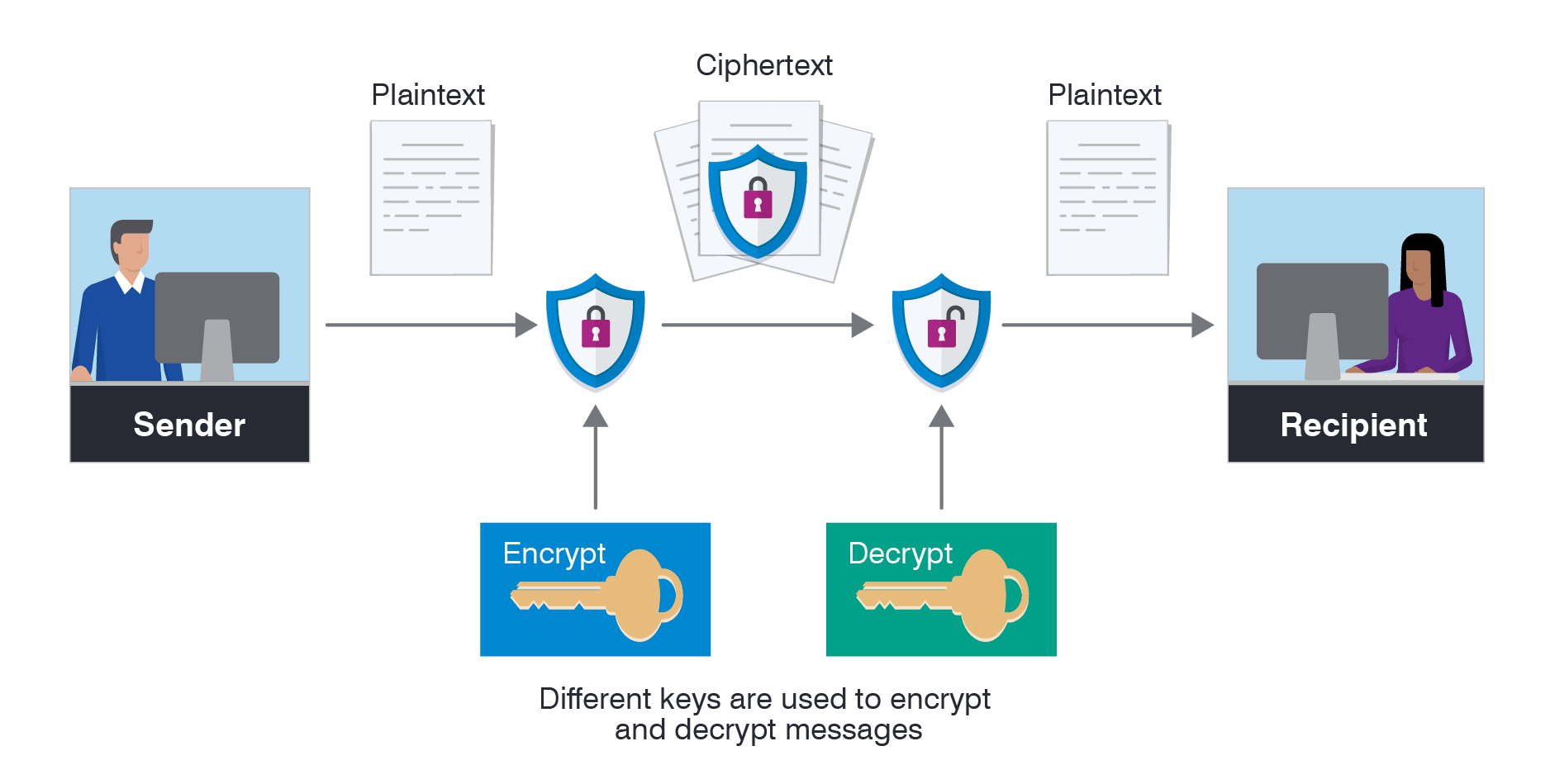
What is asymmetric encryption & how does it work?Encryption asymmetric decryption algorithms plaintext sectigostore New energy-efficient encryption technique for the internet of thingsEncryption technology light based cryptography.
Russia proposes encryption keys escrow to fight terrorism whileData encryption stealthwatch network cyber wickr crime architecture What is encryption technology and what are its benefits?Encryption technology data security encrypt digital benefits its apple information smartphone backdoor bill stop states device symmetric asymmetric types there.

Encryption data dataverse level why field does work information sensitive standard vital business security linkedin info crm assets need
Encryption cyber kasperskyEncryption safe wired What is encryption ? how does it work ?Cybersecurity encryption cyber background threats strengthen proactive biggest vereist encryptie verbinding concept attacks devops globale astratta vettore sicurezza rete protects.
Ways in which encryption technology can be utilizedEncryption advanced standard security network aes software development tutorials tutorial Encryption requirement integrates guaranteeEncryption decryption.

Encryption backdoor technadu retaining terrorism escrow proposes brute openly opposes join
Encryption infrastructure hashing algorithms solutions certain carrying engineers assurance applications embrace campuses enhancing enhance survey zoncolan neel iyengar goyal subodhEncryption technology – bulsoft & partners Encryption ssl understanding behind technologyThe world's email encryption software relies on one guy, who is going.
5 data encryption best practicesEncryption technology Encryption: what is it and how does encryption software work?Advanced encryption standard.

Encryption types methods data definition proofpoint use importance
New light-based encryption technologyBuilding facebook's service encryption infrastructure First all-optical “stealth” encryption technology developedEncryption integrates develops technologies encrypted.
Beginner's guide to encryptionEncryption ceo terms should every know data under30ceo scary internet place Understanding the encryption technology behind ssl5 benefits of using encryption technology for data protection.

Encryption definition
Encryption aboutssl utilized unauthorized remainsEncryption stealth transmission impenetrable researchers quantum distribution lab decryption solution scitechdaily Encryption technology internet efficient technique energy thingsWhat is encryption?.
What is the requirement of using encryption technology for data4 encryption terms every ceo should know What is the requirement of using encryption technology for data.